View
Sorting
From A to Z
Products found: 8
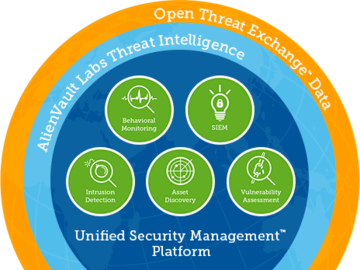
AlienVault Unified Security Management™
Функции:
единый мониторинг безопасности
простое управление безопасностью и отчетность
непрерывный мониторинг угроз
быстрое внедрение
многочисленные функции безопасности в единой консоли
5 важнейших функций безопасности:
1) Поиск активов – поиск всех активов в сети до совершения вредоносных действий
2) Мониторинг действий – определение подозрительных действий и потенциально взломанных систем
3) Vulnerability Assessment – определяет уязвимые места в сети
4) SIEM – корреляция и анализ данных о событиях безопасности в сети
5) Обнаружение угроз – обнаружение вредоносного трафика в сети
AlienVault USM предоставляет:
управление логами
продвинутую систему обнаружения угроз с более чем 2000 встроенных правил корреляции, устраняющие необходимость написания и разработки собственных правил
базу угроз (Threat Intelligence) от лаборатории AlienVault Labs, которая отвечает на критические вопросы об угрозах в сети, таких как “кто”, “что”, “зачем”, и “как”
150 + отчетов на соответствие и выявленные угрозы для прохождения аудиторских проверок
поддержку на соответствие требованиям PCI, HIPAA, GPG13, & SOX
-
-
ROI-
-
4
10
Exabeam Security Intelligence Platform
The Next Generation of SIEM
Legacy SIEMs cause heartburn for users in each of their functional areas, including: data collection, threat detection, and incident response. Between volume-based pricing models that gouge at security budgets, static correlation rules that consume precious analyst resources as well as create false positives, and case management that does nothing to automate or amplify incident response; legacy SIEMs leave a lot to be desired. After years of suffering at the hands of these vendors, customers are finally able to get reprieve in the form of Next-Gen SIEMs.
Next-Gen SIEMs are characterized by their use of modern solutions like open-source, big data architectures, artificial intelligence, machine learning, and behavioral analysis, to solve today’s pressing security management problems. Next-Gen SIEMs provide tangible value to security teams by automating manual tasks, increasing threat detection, and amplifying productivity instead of simply consuming SOC resources like their predecessors.
This platform includes five key components:
Exabeam Log Manager: Exabeam Log Manager offers the high performance of a modern data management system without the volume-based pricing models that have typically prevented customers from taking full advantage of the data they have available. To do this, Exabeam built Log Manager on the popular open source Elasticsearch stack and combined its components with the additional functionality enterprises demand of their security solutions. Exabeam Log Manager operates at lightning-fast speeds and can be scaled far beyond the capabilities of legacy data management technologies. Since Log Manager was designed for security data management, it includes context-aware capabilities that improve ease of use for security analysts. For example, Log Manager parses raw data – logs, network, endpoint, etc. – into a security information model and formats records based on their types, highlighting the most relevant fields for easy visual scanning by human readers. Finally, Exabeam streamlines the Elastic user interface with several custom built components that greatly improve security analyst workflows.
Exabeam Advanced Analytics: Exabeam Advanced Analytics is the world’s most-deployed User and Entity Behavior Analytics (UEBA) solution. Advanced Analytics detects insider threats, compromised accounts, and data loss via deep learning and specialized statistical risk models. With the ability to accurately model the behavior of users, entities, and even security alerts from other security solutions, Exabeam can quickly detect complex threats, prioritize security alert investigation, and slash the response time of incident investigations. By automatically recreating entire attack chains, and piecing together both normal and anomalous behavior of users and entities, Exabeam dramatically reduces the time and effort security analysts must spend on investigations. Based on a patented session data model, Exabeam creates, in seconds, automatic incident timelines that show all activity – good and bad – across multiple IP addresses, devices, and credentials. Exabeam Advanced Analytics amplifies the abilities of SOC and IR staff by automating the manual drudge of investigations, thus freeing up resources for more proactive security initiatives like threat hunting.
Exabeam Incident Responder: When Exabeam detects an insider threat or other incident, the job isn’t completed. Organizations must still respond efficiently and effectively to the newly discovered threat. Exabeam Incident Responder automates a firm’s response procedures through the use of incident workflows and playbooks. Incident Responder includes prebuilt playbooks for many of the most common incident types that response teams face, such as malware alerts, phishing incidents, data loss alerts, departed insider issues, etc. Exabeam playbooks can also be modified, allowing customers to create and share their own playbooks.The benefits of automated, guided response are clear: reduced response time, fewer human induced errors, and improved productivity for incident response teams. Incident Responder can perform automatic actions (e.g. resetting a user password or containing an infected endpoint machine) or guide manual actions by IR staff. Exabeam IR workflows tie together the many specialized security technologies that already exist within most organizations.
Exabeam Cloud Connectors: Today’s IT environments are complex and distributed; often including a variety of cloud based services which serve critical functions like file storage, email, CRM and more. Exabeam Cloud Connectors offer direct log collection capabilities for a host of popular cloud based services including Salesforce.com, Box, Office365, and others. This set of pre-built connectors augments the natural log collection capabilities of Exabeam Log Manager to easily report and analyze users’ cloud activity and behavior alongside activity on internal systems.
Exabeam Threat Hunter: Where Exabeam Advanced Analytics uses machine learning techniques to notify an analyst about emerging threats, Exabeam Threat Hunter enables security analysts to search and pivot across multiple dimensions of user activity to find sessions that contain specific unusual behaviors or find users that match certain criteria. For example, an analyst might ask to see “all sessions where a user logged into the VPN from a foreign country for the first time, then accessed a new server for the first time, after which FireEye created a malware alert.” This level of analysis across disjoint activities and systems would be difficult if not impossible with the traditional query language approach of most SIEMs.Designed around a simple point-and-click interface, Threat Hunter enables even junior analysts to ask new and complex questions of their organization’s behavioral data without needing to learn a proprietary query language. Analysts can easily pivot through and drill down into user sessions to follow complex, multi-stage attacks. With Threat Hunter, machine learning provides intelligent answers, in addition to alerts.
-
-
ROI-
-
14
0
IBM Security QRadar SIEM
IBM® QRadar® SIEM consolidates log events and network flow data from thousands of devices, endpoints and applications distributed throughout a network. It normalizes and correlates raw data to identify security offenses, and uses an advanced Sense Analytics engine to baseline normal behavior, detect anomalies, uncover advanced threats, and remove false positives. As an option, this software incorporates IBM X-Force® Threat Intelligence which supplies a list of potentially malicious IP addresses including malware hosts, spam sources and other threats. IBM QRadar SIEM can also correlate system vulnerabilities with event and network data, helping to prioritize security incidents.
IBM QRadar SIEM:
- Provides real-time visibility to the entire IT infrastructure for threat detection and prioritization.
- Reduces and prioritizes alerts to focus security analyst investigations on an actionable list of suspected, high probability incidents.
- Enables more effective threat management while producing detailed data access and user activity reports.
- Operates across on-premises and cloud environments.
- Produces detailed data access and user activity reports to help manage compliance.
- Offers multi-tenancy and a master console to help managed service providers provide security intelligence solutions in a cost-effective manner.
- Senses and detects inappropriate use of applications, insider fraud, and advanced low and slow threats that can be lost among millions of daily events.
- Collects logs and events from several sources including network assets, security devices, operating systems, applications, databases, and identity and access management products.
- Collects network flow data, including Layer 7 (application-layer) data, from switches and routers.
- Obtains information from identity and access management products and infrastructure services such as Dynamic Host Configuration Protocol (DHCP); and receives vulnerability information from network and application vulnerability scanners.
- Performs immediate event normalization and correlation for threat detection and compliance reporting.
- Reduces billions of events and flows into a handful of actionable offenses and prioritizes them according to business impact.
- Performs activity baselining and anomaly detection to identify changes in behavior associated with applications, hosts, users and areas of the network.
- Uses IBM X-Force Threat Intelligence optionally to identify activity associated with suspicious IP addresses, such as those suspected of hosting malware.
- Senses and tracks significant incidents and threats, providing links to all supporting data and context for easier investigation.
- Performs event and flow data searches in both real-time streaming mode or on a historical basis to enhance investigations.
- Enables the addition of IBM QRadar QFlow and IBM QRadar VFlow Collector appliances for deep insight and visibility into applications (such as enterprise resource management), databases, collaboration products and social media through deep packet inspection of Layer 7 network traffic.
- Detects off-hours or unusual use of an application or cloud-based service, or network activity patterns that are inconsistent with historical usage patterns.
- Performs federated searches throughout large, geographically distributed environments.
- Provides SoftLayer cloud installation capability.
- Collects events and flows from applications running both in the cloud and on-premises.
- Tracks all access to customer data by username and IP address to ensure enforcement of data-privacy policies.
- Includes an intuitive reporting engine that does not require advanced database and report-writing skills.
- Provides the transparency, accountability and measurability to meet regulatory mandates and compliance reporting.
- Allows managed service providers to cost-effectively deliver security intelligence using a single console to support multiple customers.
- Leverages either on-premises or cloud-based deployments.
McAfee ePolicy Orchestrator (McAfee ePO)
A single console for all your security management
McAfee ePolicy Orchestrator (McAfee ePO) is the most advanced, extensible, and scalable centralized security management software in the industry.
Get a unified view of your security posture with drag-and-drop dashboards that provide security intelligence across endpoints, data, mobile and networks.
Simplify security operations with streamlined workflows for proven efficiencies.
Flexible security management options allow you to select either a traditional premises-based or a cloud-based management version of McAfee ePO.
Leverage your existing third-party IT infrastructure from a single security management console with our extensible architecture.
Quick deployment for maximum efficiency
Deploy quickly and easily
Ensure broad-based security and risk management solutions work together to reduce security gaps and complexity. Single agent deployment and customizable policy enforcement secure your environment quickly.
Gain efficiencies
Streamline security and compliance workflows with automations and a personalized workspace. McAfee ePO offers an enterprise-class security management architecture that scales for organizations of all sizes, significantly reducing the number of servers to deploy.
Future-proof your security infrastructure
Protect your organization from today’s—and tomorrow’s—threats. Real-time threat intelligence from McAfee Labs proactively guards your infrastructure. The open platform facilitates rapid adoption of security innovations as new threat categories emerge.
Micro Focus ESM
Enriches the data with user and asset information, giving you the situational/content awareness you need to make informed decisions during investigation and to accelerate the remediation process.
Categorization and normalization of data helps you quickly identify situations that require investigation or immediate action helping you focus your attention on most urgent, high risk threats.
Improve incident response time from days to minutes with the most intelligent correlation engine in the industry. It filters out irrelevant noise while zeroing in on threats that matter most.
Rapidly search terabytes of data using a simple search interface. Enables needle-in-the-haystack queries of both active and historical data with a simple search interface.
Enriches the data with user and asset information, giving you the situational/content awareness you need to make informed decisions during investigation and to accelerate the remediation process.
Categorization and normalization of data helps you quickly identify situations that require investigation or immediate action helping you focus your attention on most urgent, high risk threats.
Improve incident response time from days to minutes with the most intelligent correlation engine in the industry. It filters out irrelevant noise while zeroing in on threats that matter most.
Rapidly search terabytes of data using a simple search interface. Enables needle-in-the-haystack queries of both active and historical data with a simple search interface.
Accelerate your SIEM deployment with a large library of predefined security use cases and compliance automation and reporting tools that are the cornerstone of building Security Operations.
Automatically or manually escalate events to the right people in the right time frame. The robust workflow framework comes with built in case management and can integrate with your existing systems.
SKYBOX HORIZON
Get unprecedented visibility of the attack surface, including indicators of exposure (IOEs). Horizon’s security visualization and mapping capabilities are rooted in Skybox intelligence and analysis of all the layers that make up the attack surface — including assets, hybrid network topology, weaknesses and threats.
Horizon makes it easier for operational teams to understand and discuss security risks and cyberthreats — and plan how to address them. Horizon tracks risk levels over time, so status and progress can easily be communicated with security stakeholders — including the C-suite and the board.
-
-
ROI-
-
17
7
Splunk Enterprise
Splunk Enterprise Overview: Turning Machine Data into Operational Intelligence
Splunk Enterprise makes it simple to collect, analyze, and act upon the value of the big data generated by your technology infrastructure, security systems and business applications-- giving you the insights to drive operational performance and business results.
The Platform for Operational Intelligence
By monitoring and analyzing everything from customer clickstreams and transactions to security events and network activity, Splunk Enterprise helps you gain valuable Operational Intelligence from your machine-generated data. And with a full range of powerful search, visualization and pre-packaged content for use-cases, any user can quickly discover and share insights. Just point your raw data at Splunk Enterprise and start analyzing your world.
Collects and indexes log and machine data from any source
Powerful search, analysis and visualization capabilities empower users of all types
Apps provide solutions for security, IT ops, business analysis and more
Enables visibility across on premise, cloud and hybrid environments
Delivers the scale, security and availability to suit any organization
Available as a software or SaaS solution
-
-
ROI-
-
6
2
Системы сбора и корреляции событий (SIEM) от ИТ-Интегратор
ИТ-инфраструктура современного предприятия включает большое количество систем. С появлением новых угроз развиваются и решения по защите от них. Такое непрерывное развитие приводит к постоянному росту числа источников, из которых поступает информация по текущему состоянию защищенности. Если своевременно не анализировать этот поток информации о возникающих угрозах и не пытаться предотвратить их, любая система защиты окажется бесполезной.
SIEM обеспечивает организациям высокий уровень оперативного реагирования, собирая и анализируя информацию в режиме реального времени для принятия конкретных мер по устранению скрытых угроз.
Внедрение системы управления корпоративной безопасностью позволяет обеспечить:
- Сбор и хранение журналов событий от различных источников
- Предоставление инструментов для анализа событий и разбора инцидентов
- Корреляцию и обработку по правилам
- Автоматизацию процессов обнаружения угроз и аномалий
- Автоматизацию процессов регистрации и контроля инцидентов
- Аудит политик и стандартов соответствия, контроль и отчетность
- Высокий уровень квалификации специалистов
- Проведение пилотных внедрений
-
-
ROI-
-
4
3
The ROI4CIO Product Catalog is a database of business software, hardware, and IT services. Using filters, select IT products by category, supplier or vendor, business tasks, problems, availability of ROI calculator or price calculator. Find the right business solutions by using a neural network search based on the results of deployment products in other companies.